Slack space
Slack space refers to portions of a hard drive that are not fully
used by the current allocated file and which may contain data from a
previously deleted file
llustration of slack space on a hard drive
In the example above, saving a 768 byte file (named User_File.txt)
requires only sector 1 and 1/2 of sector 2 in the cluster.
Depending on the operating system, the remaining 256 bytes in sector
2 might be filled with 1′s or 0′s or might simply remain intact.
Both sectors 3 and 4 would not be overwritten and are thus considered
slack space. If the slack space previously contained data from
a deleted file, this information could be recovered with forensic
tools.
Additional Details Operating systems allocate files on
a hard drive using clusters, which are a collection of contiguous
sectors. Because a cluster is the smaller allocation unit an
operating system can address, if a file does not utilize the full
cluster, a portion of the space remaining may not be overwritten and
might contain data from a previously deleted file. For forensic
analysts, it is important to understand that slace space is
considered allocated space since it is part of an allocated cluster.
As such, special tools must be used to extract and analyse slace
space. An analysis of unallocated data will not contain any
slack space data.
unallocated space
Unallocated space, sometimes called “free space”,
is logical space on a hard drive that the operating
system, e.g Windows,
can write to. To put it another way it is
the opposite of “allocated” space, which is where the operating
system has already written files to.
Examples.
If the operating system writes a file to a certain space on the
hard drive that part of the drive is now “allocated”, as the
file is using it the space, and no other files can be written to that
section. If that file is deleted then that part of the hard
drive is no longer required to be “allocated” it becomes
unallocated. This means that new files can now be re-written to
that location.
On a standard, working computer, files can only be written to the
unallocated space.
If a newly formatted drive is connected to a computer,
virtually all of the drive space is unallocated space (a small amount
of space will be taken up by files within the file system, e.g $MFT,
etc). On a new drive the unallocated space is normally zeros, as
files are written to the hard drive the zeros are over written with
the file data
Working Example
Blank Drive
A freshly formatted (NTFS) 500 GB hard drive starts with
99.9% unallocated space; we will assume its 100% to make the
maths slightly easier. All of the unallocated space will be zeros,
literally 00 00 00 written on the hard drives.
If a 5 GB file, e.g a large movie, is placed on the drive, then
there will be 1% (5 GB) allocated space and 99%
unallocated (495 GB)
If a 10 GB database file is now added to this hard drive
there will be a total of 3 % (15 GB) of allocated space and 485 GB
unallocated space. New files will only be written into the remaining
unallocated space.
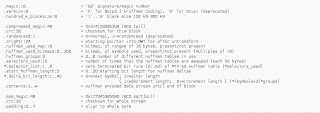
magic number
A
magic number is a number embedded at or near the
beginning of a file that indicates its
file format (i.e.,
the type of file it is). It is also sometimes referred to as a
file
signature.
Magic numbers are generally not visible to users. However, they
can easily be seen with the use of a hex editor, which is a
specialized program that shows and allows modification of every
byte in a file.
For common file formats, the numbers conveniently represent the
names of the file types. Thus, for example, the magic number for
image files conforming to the widely used GIF87a format in
hexadecimal (i.e., base 16) terms is 0x474946383761, which when
converted into ASCII is GIF87a. ASCII is the de facto
standard used by computers and communications equipment for
character encoding (i.e., associating alphabetic and
other characters with numbers).
Likewise, the magic number for image files having the subsequently
introduced GIF89a format is 0x474946383961. For both types of GIF
(Graphic Interchange Format) files, the magic number occupies the
first six bytes of the file. They are then followed by additional
general information (i.e., metadata) about the file.
Similarly, a commonly used magic number for JPEG (Joint
Photographic Experts Group) image files is 0x4A464946, which is the
ASCII equivalent of JFIF (JPEG File Interchange Format). However,
JPEG magic numbers are not the first bytes in the file; rather, they
begin with the seventh byte. Additional examples include 0x4D546864
for MIDI (Musical Instrument Digital Interface) files and
0x425a6831415925 for bzip2 compressed files.
Magic numbers are not always the ASCII equivalent of the name of
the file format, or even something similar. For example, in some
types of files they represent the name or initials of the developer
of that file format. Also, in at least one type of file the magic
number represents the birthday of that format's developer.
Various programs make use of magic numbers to determine the file
type. Among them is the command line (i.e., all-text mode)
program named
file, whose sole purpose is determining the file
type.
Although they can be useful, magic numbers are not always
sufficient to determine the file type. The main reason is that some
file types do not have magic numbers, most notably plain text files,
which include HTML (hypertext markup language), XHTML (extensible
HTML) and XML (extensible markup language) files as well as source
code.
Fortunately, there are also other means that can be used by
programs to determine file types. One is by looking at a file's
character set (e.g., ASCII) to see if it is a plain text file. If it
is determined that a file is a plain text file, then it is often
possible to further categorize it on the basis of the start of the
text, such as
<html> for HTML files and
#! (the
so-called
shebang) for
script (i.e., short program)
files.
Another way to determine file types is through the use of filename
extensions (e.g.,
.exe,
.html and
.jpg),
which are required on the various Microsoft operating systems but
only to a small extent on Linux and other Unix like operating
systems. However, this approach has the disadvantage that it
relatively easy for a user to accidentally change or remove the
extensions, in which case it becomes difficult to determine the file
type and use the file.
Still another way that is possible in the case of some commonly
used filesystems is through the use of file type information
that is embedded in each file's metadata. In Unix-like operating
systems, such metadata is contained in inodes, which are data
structures (i.e., efficient ways of storing information) that
store all the information about files except their names and
their actual data.
Magic numbers are referred to as
magic because the purpose
and significance of their values are not apparent without some
additional knowledge. The term
magic number is also used in
programming to refer to a constant that is employed for some specific
purpose but whose presence or value is inexplicable without
additional information.
File structure on Borland Delphi 7
When we create
a new project and then save it then we will get RecentMost file
appears on the folder where the project disimpan.File new-file
are:
1. *. Cfg Contains about the configuration file.
2. *. Dof
Contains the options of a project That is expressed through selection
Project | Options
3. *. Dsk Contains the options of a project That
is expressed through selection Tools | Environment Options.
4. *.
Res Binary file containing icons used by the project.
5. *. Dcu
Unit already been compiled, this file appears when Delphi project has
been compiled.
6. *. Dfm Storing information Relating to the
form.
7. *. Dpr Storing information Relating to the form.
8. *.
Pas Place source code is stored.
MP3 files are composed of
multiple MP3 frames which consist of the MP3 header and the data
MP3.Frame are independent items: one can cut a frame from the file
and the MP3 player will be the actual payload.Diagram
memainkannya.Data MP3 audio shows that the MP3 header consists of a
sync word used to identify the initial frame valid.Ini followed by a
little show that this is the MPEG standard and two bits that indicate
that layer 3 is used, then the MPEG-1 Audio layer 3 or MP3.Setelah
this, the values will differ depending on the file MP3.Kisaran
value for each part of the header along with the header
specifications defined by ISO / IEC 11 172-3.Kebanyakan MP3 files
today contain ID3 metadata which precedes or follows the MP3 frames;
are also shown in the diagram.
Structur File .bz2
A
.bz2 stream consists of a 4-byte header, followed by zero
or more compressed blocks, immediately followed by an end-of-stream
marker containing a 32-bit CRC for the plaintext whole stream processed.
The compressed blocks are bit-aligned and no padding occurs.
Because of the first-stage RLE compression (see above), the maximum
length of plaintext that a single 900 kB bzip2 block can contain is
around 46 MB (45,899,235 bytes). This can occur if the whole plaintext
consists entirely of repeated values (the resulting
.bz2
file in this case is 46 bytes long). An even smaller file of 40 bytes
can be achieved by using an input containing entirely values of 251, an
apparent compression ratio of 1147480:1.